Supply chain attack: When cyber attacks come via update
An attack on the IT supply chain aims to manipulate the production process of a third-party software from development to updating, so that malicious code is pushed out instead of an update. This IT supply chain is vulnerable and cyber criminals are increasingly attacking it. That's because such a supply chain attack is efficient for them: if they can manipulate vendors' software packages and platforms [...]

Supply chain attack locations
A compromised supply chain is difficult for affected customers to detect. Therefore, cyber criminals have enough time to cause damage - such as data exfiltration, attacks on systems or disrupting processes. These attacks are different from previous attacks targeting individual customers and pose a challenge even for experts. It is not for nothing that the European Union Agency for Cybersecurity estimates, ENISAThe risk is high even for companies whose IT defenses are actually quite well established.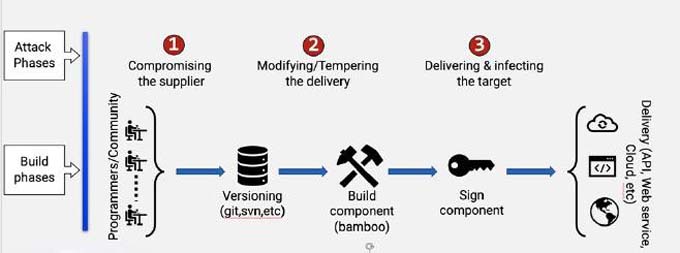
- Phase One - Programming: These attacks are relatively easy to detect. They start via targeted mails, exploits and malicious websites to gain access to the programming code. It is relatively easy for a hacker to change the code at that point. But what they have changed is visible in the logs.
- Phase Two - Versioning: Attackers can drive an attack via a remote desktop protocol (RDP) with little effort. Weak passwords and exploits of an application help them to do so. They can also have modified versions rolled out in a reduced or delayed scope, because they have direct access to source code and logs and leave few traces. But the modified code proves the manipulation.
- Phase Three - Implementation (Build): This is where it gets more challenging for the hackers, but unfortunately also for the defenses. The means are the old ones and attackers use RDP attacks, weak passwords and exploits in the application. But they need a good understanding of scripts. This is because the necessary modifications to individual builds take a lot of time and are complex. The modified code can be hidden. The defense would also have to check the successive script versions individually to detect manipulations.
- Phase Four - Signing the components: If the attacker gets involved now, he does not have to manipulate code. He simply replaces the actual code with malicious code. But a validation in the supply chain concept will reject this fake update. Hackers must therefore meet some minimum criteria for legal updates in their fake programs.
- Phase Five - Delivery: Here, too, an attacker only has to exchange the components. But the malicious components then have no signature and can be recognized by it.
How can SMEs protect themselves?
Although the attacks take place in the update supplier's supply chain, the attacks also affect smaller and medium-sized companies. To arm themselves against the damage of a supposedly legal update, they should follow these measures:- A Implement comprehensive cybersecuritywhich includes Endpoint Detection and Response (EDR), but which, thanks to Threat Intelligence, also sees and reports suspicious data connections. After all, a common symptom of a successful supply chain attack is communication with a malicious command-and-control server. Companies with limited IT resources in particular should also consider a managed detection and response (MDR) service, and with it the expertise and time of IT security analysts. Only by combining EDR and MDR can managers see anomalies as they occur.
- Equally important is Educating employees about phishing, to prevent the hijacking of an identity in the supply chain process.
- It is central to Know and continuously review a company's supply chain processes. Does an IT manager even know which software or service updates it obtains from whom and when? What hardware does it acquire and how is it protected from receiving malware through this? Every security manager should ask the following questions of his IT supplier: - Is the vendor's software/hardware development process documented, traceable and verifiable? - Is fixing known vulnerabilities factored into product design and architecture, runtime protection and code review? - How does the vendor keep a customer informed of emerging vulnerabilities? - What capabilities does the supplier have to address "zero-day" vulnerabilities - those vulnerabilities that are designed into software from the beginning and are not discovered until later? - How does the supplier manage and monitor the production processes of a software and an update? - What does the supplier do to protect its updates from tampering and malware? - What kind of background checks are performed on the vendor's staff and how frequently? - How secure is the rollout of updates?
This article originally appeared on m-q.ch - https://www.m-q.ch/de/supply-chain-attacke-wenn-cyber-angriffe-per-update-kommen/









